

The Key Benefits of all-in-one
Cyber Business Package
All you need is in one package
Created by a group of experts specifically to cover essential cybersecurity and compliance needs for small and
medium-sized businesses.
Simple sign-up and user-friendly interface engraved by high-quality endpoint security and antivirus software.
Cyber Insurance support with a cover-up to €1,000,000.
A dedicated account manager is always at your service.
Emergency Cyber Response Hotline is open 24x7x365.

Fix Vulnerabilities

Save Money

User-friendly Interface

Get Cyber Insurance Support
.png)
The World's Leading Cybersecure Data Enrichment
We transform raw data into actionable intelligence.
From datasets for AI training to real-time market APIs and ready-to-use business tools, we provide a tailored approach for each client.
AI Product Tagging
Instantly enhance search, filtering, and product detail pages.
Discovery Essentials
Must-have AI tools for powerful product discovery
What is included in your cybersecurity business package
The services we provide

AI-Powered
Security Assessment
BCG’s AI can identify vulnerabilities and suggest what cybersecurity solutions can fix them.

Free Online Consultation
Based on the results of the cyber report, you can schedule a consultation with a cybersecurity expert.

Incident Response Services
You can call the Emergency Response Hotline.
Our partners operate in 35 countries.

Money saving
We help you to avoid overpaying for unrelated cybersecurity products and services.
.png)
Receive threat alerts directly on your phone, available on IOS and Android.
By email or phone.
The security incident handling service line is open 24x7x365
Our partners’ team of over 130 cybersecurity specialists provides a range of proactive security services as well as post-event remediation to get our customers back online fastThe quickest response rate in the industry
Cyber Attack Emergency Response Service
.png)
Your primary point of contact who will work with you closely to understand your project needs, and ensure smooth execution and high-quality results.
At any time, you can schedule a consultation with a cybersecurity expert.
One of the quickest response rates in the cybersecurity industry
Tailored client-oriented approach
.png)
The Executive Summary report provides an overview of all devices and their statuses and threats, as well as at-a-glance values for threats, patches, and devices.
The Device report provides a complete list of devices with details such as their operating system, status, and subscription data.
The Task report provides a summary of the tasks executed on your devices within a defined time frame.
The Audit log report provides insight into various user and system activities such as policy changes, user access changes, installer downloads, etc.
The Antivirus threat report provides information on threats found on your devices within a defined time frame.
The Web Control report provides details on all web traffic recorded on your devices within a defined time frame. This report is available at site level only.
The USB Protection report provides an overview of all removable storage device connections to devices. This report allows you to monitor which devices were blocked and allowed across the company. When an end user reports a blocked connection (due to policy settings), the USB Protection report can help determine if the device in question needs to be allowed.
Cybersecurity reports

Simple Customer journey
DEMO CALL
Cyber Assessment


Creating a client data room

Implementation of cyber security software

Getting cyber
insurance

ENHANCED
CYBERSECURITY
.png)
Blog
Latest blog
BCG has developed
simple & affordable cybersecurity solution
for your growing business
.png)

Get online protection you can trust from one of the leaders in cybersecurity. BCG business package provides high-quality endpoint security and antivirus software to small and medium businesses.
We act as partners to our customers, helping them improve their cyber risk posture by providing our easy-to-use cybersecurity solutions that provide strong protection against a wide variety of cybersecurity threats so that you can worry less and focus more on your business.

Penetration Testing
Vulnerability Scanner

Our partner's in-house team pen-testers are certified industry experts with years of experience and education.
An automated vulnerability scanning platform will keep you secure and compliant.
We deliver accurate and actionable reports for your unique environment.
Phishing emails: how to recognize them and avoid being scammed

24 May 2024
How to protect your data in case of a leak: advice from a cybersecurity expert

24 May 2024
Protection against Cyber Attacks: Guaranteeing Security in the Internet World
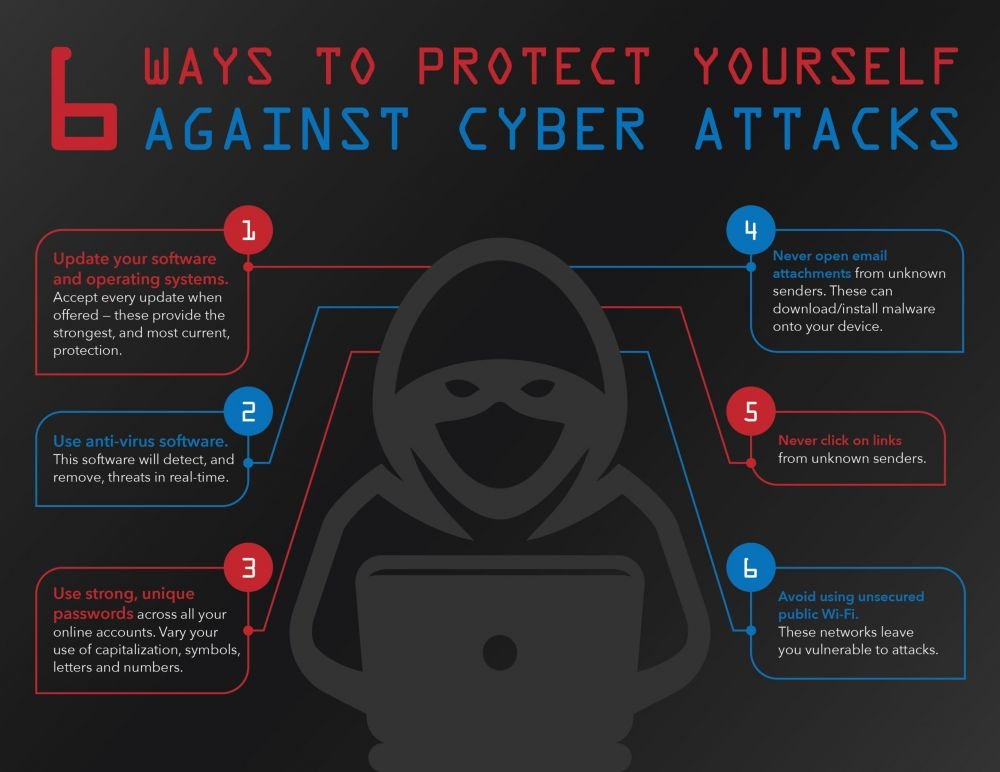
24 May 2024
How to teach children cybersecurity

24 May 2024

How cybercrime may affect your organisation

leakage of sensitive information
Organisation secrets can be stolen

Financial losses
Money can be stolen, converted into cryptocurrencies and passed through a mixer to mask further trace

Operational disruption
Corporate data can be encrypted or destroyed. This can lead to a freeze in all your organisation's operational activities

Lost revenue
Impact the relationship between the company
and its customers

Reputational damage
Customers, and even suppliers, may feel less secure leaving their sensitive information in the hands of a company whose IT infrastructure was broken at least once before

Legal consequences
Non-compliance with data protection regulations and laws can result in legal actions, fines, and penalties, increasing financial burden and further damaging the organization’s reputation
Our partners' awards






.png)
Monitor emerging cyberthreats in real time via a cloud-based console you can access from your web browser on any device with Avast Business Hub. Plus, manage all your Avast Business security services and subscriptions from one central online hub and view comprehensive reports.
Help to protect your Windows PC, Mac, and Windows Servers against malware infections and zero-day threats. This includes File Shield and Web Shield. Plus, Mail Shield scans in and outgoing emails for malicious content, real-time Behavior Monitoring checks endpoints for suspicious activity or code, and Cloud Sandbox runs untrusted applications in a safe environment for you and more.
Go further to help protect your business and customer data from breaches, ransomware encryption, or theft with powerful cybersecurity technology. This includes our Firewall, Ransomware Shield, Remote Access Shield, and more.
Do more to help your employees avoid fake websites that steal sensitive data like usernames, passwords, and credit card details. Our Real Site technology is purpose-built to defend employees against DNS (Domain Name System) hijacking.
Create a safer, more productive business environment for you and your employees by controlling their access to potentially dangerous or non-work-related websites through web domain and content filtering.
Secure any business data your employees transmit over any internet connection, including public Wi-Fi. With no data limits, our built-in personal VPN also has the potential to boost productivity.
Reduce the chances of your business experiencing data theft, data loss, or endpoint malware infections caused by external hardware. Block unauthorized or unrecognized USB storage devices from connecting to endpoints with ease.
Premium Business
Cybersecurity Software
.png)
A reactive service offering an immediate, technical response to a real or suspected cyber event. This usually includes a team of forensic analysts, cyber security engineers, ransom negotiators and business resumption specialists that triage the incident, contain the threat and repair systems to get the business back online.
Insurance coverage varies depending on your cyber insurance policy.
UK and European registered businesses with a turnover under € 20m are entitled to Cyber Liability Insurance.
BCG’s partner represents you in the discussion with all insurers and negotiates for you the most advantageous offers, depending on your needs.
You no longer have to take out 3 policies and pay 3 times more; now all the responsibilities you need can be combined and included on our policy. We can make cost reductions of up to 60%;
Through the discussion with the BCG’s partner consultants, you will find out which are the best solutions for you on the national and international market;
Claims Assistance – BCG has created an internal claims department to support all customers regardless of the insurer and insurance product chosen.We will contact you in maximum 24 hours and you will work directly with our colleagues who are in contact with the best insurance specialists dedicated to the IT field.
-
Cyber incident response costs to quickly neutralise
-
or minimise the damage caused by a cyber event
-
Your losses as a result of:
-
Privacy breach notification costs
-
Lost, corrupted or inaccessible electronic data
-
System damage
-
System business interruption
-
Claims made against you arising out of:
-
Invasion of privacy
-
Network security liability
-
Cyber and privacy liability
-
Management liability arising from a cyber attack
-
Defamation
-
Intellectual property rights infringement
-
Additional covers
-
Insurable fines and penalties
-
Court attendance costs
-
-
You must provide all information which may be relevant to the cover in a clear and accessible manner and as accurately and
completely as possible. -
You must notify us of any incident, circumstance or claim in accordance with the conditions detailed in the policy document.
-
You must not admit liability for or settle or make or promise any payment or incur any costs and expenses without our prior
written agreement. -
You must maintain all your rights of recovery against any third party and make these available to us where possible.
-
The cover is underwritten by CFC Europe S.A. and administered by the Leader Team Broker. CFC Europe S.A. is authorised and regulated by the Financial Services and Markets Authority (FSMA). Registered number: 0711818068.
Cyber Liability Insurance
This is the only policy in the world that provides global coverage with an A+ rating and includes proactive protection against hacking attacks.
Backed up by insurers from Lloyd's market.
