
BLOG
Protection against Cyber Attacks: Guaranteeing Security in the Internet World
What to do if your business is subject to a cyber attack? find out about main steps that will help to you fast to react on threats and minimize damage . Our recommendations will help to you stay ahead cybercriminals .
Cybercrime knows no boundaries. It continues to threaten users, organizations and states around the world, increasing its strength and accuracy. According to research, in 2021 the number of attacks on corporate networks has increased by half compared to the previous year. In addition to direct financial losses, cybercrime causes enormous damage to organizations, eroding their reputation and customer trust.
Who's Under Threat: Everyone, from Small to Large
If it seemed that cybersecurity was only of interest to large organizations, this is a strong misconception. Everyone - from individuals to companies of all sizes - needs protection from cyber threats. Cybercrime is so common that it is simply impossible to ignore this fact.
What is a Cyber Attack?
A cyber attack is an attempt by attackers to attack computers, steal data, or use compromised systems for additional fraud. These attacks are becoming increasingly sophisticated, making prevention a critical concern for everyone.
Exploiting Vulnerabilities: Home Tactics of Cybercriminals
Cybercriminals look for and find weak points in systems to cause damage. This imbalance in the fight for security gives an advantage to attackers; often even large companies cannot completely protect themselves from attacks.
Diversity of Cyber Attacks: Threat From All Sides
Cybercriminals use a variety of attack methods, including malware and distributed DDoS attacks.
Types of Cyber Attacks: What Threats Exist?
Malware: Secret Computer Visitors
Malicious software is created to be injected into devices and subsequently used by attackers. It can sneak in unnoticed and harm users, including through ransomware, Trojans, and spyware.
Distributed DDoS Attacks: When Systems Are Overloaded
These attacks aim to overload targeted resources, making them unavailable to normal users. They create huge flows of data that can cause disruptions in the systems being attacked.
Phishing
Phishing attacks are becoming increasingly sophisticated, where scammers posing as trusted individuals seek to gain access to valuable information by distributing malicious links or attachments via email or other communication channels. This becomes a serious security threat for both individuals and organizations.
Spear Phishing: The Threat of Targeted Attacks
Phishing can be targeted at specific users or organizations, including whaling attacks targeted at senior company management. These could be attempts to compromise corporate email to extort money or obtain valuable information.
Financial Damage: Results of Phishing Attacks
Corporate email compromise attacks have resulted in huge financial losses. Damages totaled $43 billion over a five-year period, according to FBI data.
Fighting Cyber Attacks: Diverse Threats in the Internet World
SQL Injection Attacks: Website Vulnerability
Many websites operate on databases, making them a target for SQL injection attacks. Attackers use carefully crafted requests to gain access to valuable data or personal information.
Cross-Site Scripting (XSS): Injecting Malicious Code
XSS attacks allow attackers to inject malicious code into a web application, which can lead to theft of session files, distribution of malware, and other malicious actions.
Botnets: Managed Network of Infected Devices
Botnets are used to send spam, create DDoS attacks and other cybercrimes. With their help, attackers gain access to the computing resources of devices, which makes them a powerful tool for cyber attacks.
Responding to Cyber Attacks: Steps Towards Protection
Team Mobilization: Quick Action for Safety
Security personnel must be deployed quickly to counter the attack.
Determining Attack Type: Understanding the Enemy
Determining the type of attack will help you focus on the necessary measures to stop it.
Containing the Attack: Stopping the Spread
Identifying and blocking all access routes for attackers is a top priority.
Damage Assessment: Restoring Safety
Determining the scope of the attack and eliminating vulnerabilities will help restore system security.
Response to a Cyber Attack:
Report a Cyber Attack: Notifying Authorities and Clients
Once you discover a cyberattack, it is important to immediately report it to the appropriate authorities depending on your company's jurisdiction. If you have cyber insurance, contact your insurance company for further instructions. It is also necessary to notify customers, especially if their data has been compromised. If necessary, issue a press release to inform the public about the event. Honesty and transparency in communication will help maintain customer trust.
Bug Fixing: Training and Improving Systems
After an attack, conduct an investigation and identify improvements to systems and processes that will help minimize the risk of a repeat incident. Use this experience to strengthen your company's cybersecurity.
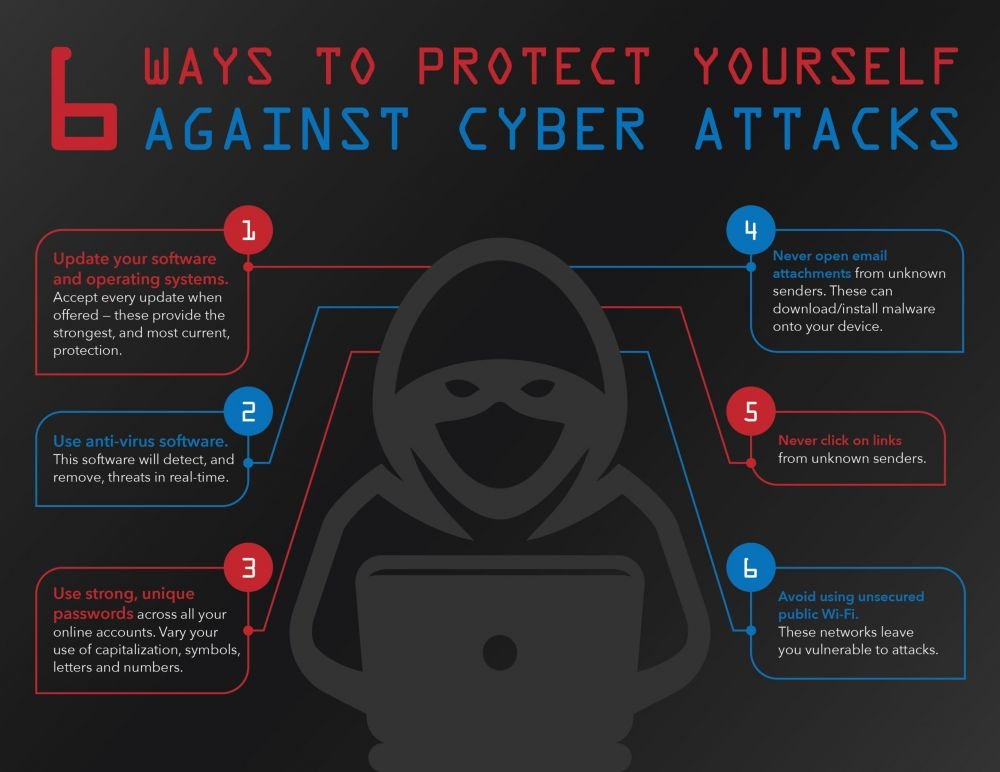
Preventing Cyber Attacks: Effective Defense Measures
Employee Training: Cyber Hygiene Training
Regular cybersecurity training can help employees develop good habits, such as checking links and email addresses before clicking them and being careful when sharing sensitive information.
Encryption and Backup: Data Protection
Encrypting all sensitive data and creating regular backups will help prevent data leakage and loss in the event of a cyber attack.
Regular Security Audits: Monitoring and Evaluation
Periodic security audits will help identify vulnerabilities and ensure your company's cyber defenses are strong.
Access Management: Restriction and Control
Setting data access restrictions and installing multi-factor authentication will help prevent unauthorized access to systems.
Update and Password Policy: Security Measures
Regularly updating software and using strong passwords with multi-factor authentication will help protect systems from cyber attacks.
Firewall: Network Protection
Placing your network behind a firewall will help prevent brute force attacks and keep your network secure.
Frequently Asked Questions about protection against cyber attacks
How can companies effectively respond to cyberattacks, from immediate actions during an attack to strategies to prevent and mitigate risks in the future?
To effectively respond to cyberattacks, companies need to have a plan of action that includes quickly mobilizing the security team, identifying the type of attack, stopping the spread of the attack, and assessing the damage. After an attack, it is important to analyze what happened, make security improvements and develop measures to prevent future incidents.
In what ways do a variety of cyberattack methods, such as malware and distributed DDoS attacks, pose a threat to both individuals and businesses, and how can these threats be countered?
A variety of cyberattack methods allow attackers to target systems in a variety of ways, creating multiple vulnerabilities for both individuals and businesses. To combat these threats, a comprehensive approach that includes updating software, installing anti-virus software, and security awareness training for employees is necessary.
Discuss the importance of cyber hygiene training for employees and its role in mitigating the risk of cyber attacks within organizations.
Cyber hygiene training for employees plays a key role in preventing successful attacks since most attacks start with social engineering or user error. This training includes safety rules for handling email, links and attachments, as well as adherence to rules for handling sensitive information.
How have cyberattacks evolved in their complexity and what challenges does this present for individuals and organizations in terms of prevention?
Cyberattacks are becoming increasingly sophisticated and targeted, utilizing new methods and technologies. This means that preventing attacks is becoming a complex task that requires constant updating of technical defenses and user awareness.
What are the consequences of cybercrime spreading across geographical boundaries and how does this affect global security?
Borderless cybercrime poses a threat to all Internet users, organizations and nations. This increases the complexity of protecting information systems and requires international cooperation to combat this threat.



